Welcome to the ConnectWise ScreenConnect Feature Request Portal
If you do not have an account, click "Sign in/ Sign up" to get started.
Tips
- Search for an existing improvement or feature request before adding your own. This helps us prevent duplicate entries and track all suggestions.
- If you find a matching request, give it a thumbs up and throw in a comment.
- If you can't find a request for an item you need, create your own request. Provide as many details as you can, especially regarding possible use cases.
Rules
- No spam, advertising, or self-promotion.
- No offensive posts, links, or images.
- Only one request per post.
- Administrators have the ability to moderate the forums, including editing, deleting, and moving posts. Posts may be deleted for any reason, with or without notification.
Thank you for sharing your thoughts with us!

report manager reports emailed on a schedule task
I noticed report manager has a new feature to directly send the report in a email attachment. It would be cool if you could schedule that on a reoccuring task.

Web Maintenance Mode has different defaults than the Application Maintenance Mode
In the application maintenance mode, the default is to Ignore Alerts, but NOT Ignore Scripts.
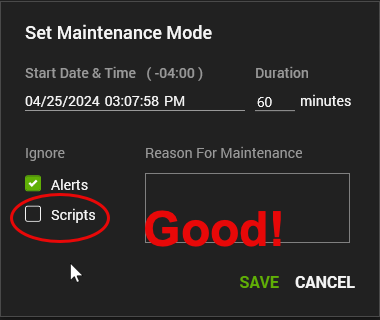
In the Web setting for maintenance mode, it is set to ignore BOTH by default.
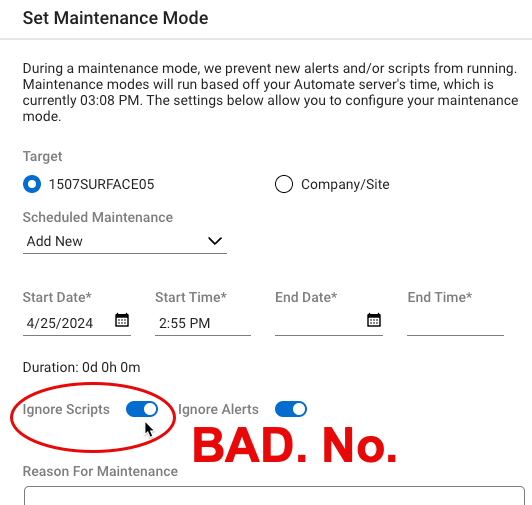
Can we please change the web maintenance mode to match the original application maintenance mode?

Support for connecting to a headless endpoint (windows computer without a monitor plugged in).
Currently there is no support for connecting to a headless endpoint (windows computer without a monitor plugged in). This is a big problem, as we are in the middle of moving from Bomgar to Control and now we realize that we can't support many of our client's servers or even Win10 computers who are headless. Even though the client has no monitor connected, we should still be able to see the Explorer GUI, other remote support apps certainly can do this. This is a HUGE feature-lack.

Support X-Forwarded-For headers
Due to insurance and industry requirements we are required to host CW Control behind an approved WAF/Proxy. But in doing so all WEB activity is logged with the WAF/proxy IP instead of the endclient IP. This decreases the value of the built-in CW Control logging and triggers functionality.
Support has confirmed that CW Control does not currently support X-Forwarded-For (XFF) which is a de-facto web standard for passing client IPs through web Proxies. Can we get this header feature added? https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/X-Forwarded-For
I was told Control is unable to read the header response so I wouldn't be able to manually enable it via "Security Toolkit" > "ExtraSecurityHttpHeadersList".
Thanks,

Thanks for your request, after speaking with our Architecture team I have registered this request for future consideration.
The key concern is that the product would have to become much more aware of the reverse proxy sitting in front of it in order to properly handle the traffic in a secure manner.

Sort options for Access Computers list/section
Under "Access" for the unattended with the agent installed, it would be nice to be able to have sort/search options for the list to sort by computer name, user, for example. I know I can create groups that allows for filters, but some sorting options would be VERY convenient (unless I'm totally missing something and it exists already... ?)
User Read Receipts
Is there anyway we can use the existing read-receipts from Microsoft 365 / Outlook to send read receipts through Manage? That way we know when a user has read the email?

Variable time limit on time based 2fa tokins.
Set the time deviation for time based 2fa to be variable so you don't repeatedly get refused when your phone time doesn't match perfectly with computer or server time. Verizon locks time about 20 seconds off from actual time and this causes a lot of bad 2fa codes. If we can adjust this variable to have some wiggle room this would no longer happen.

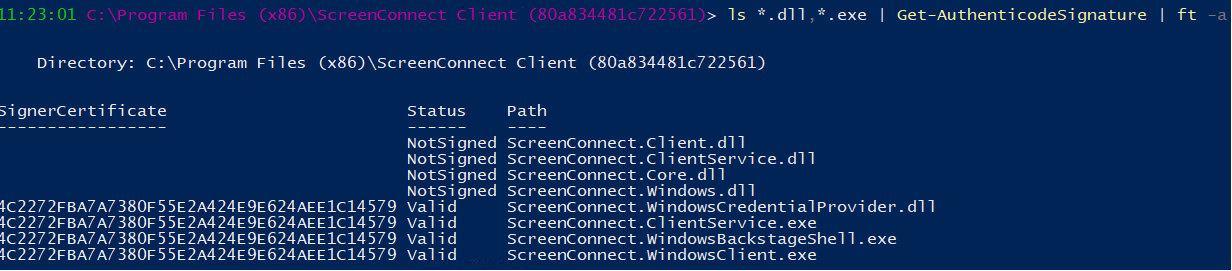
Code sign Connectwise Control .dll's
When a new version of the Screenconnect client is released & installed, Microsoft Defender for Endpoint - Attack Surface Reductions' rule "Block executable files from running unless they meet a prevalence, age, or trusted list criterion" denies the libraries from being used as they have no reputation.
This is expected behavior as a new version of the client being released globally is seen as "unknown" by Microsoft Security products.
The executables are not being flagged as low reputation as they are digitally signed & Microsoft have "established trust" with the code signing certificate in use.
Our request is to please sign the .dll's as well, without this digital signature, Microsoft wont "trust" the new files straight away which causes issues until enough devices globally have the client installed & Microsoft's systems learn / trust them.
It also enables us to create a trusted code signing certificate "Indicators", excluding any executable & dll from ASR rules etc, preventing these types of issues.
Support case reference #01401061

Shared Clipboard from host to remote session pasting numbers as a picture.
Not sure if there was an recent update to connectwise but copying a cell from excel file on host computer to paste into remote session excel file it tries to paste as picture and not the contents. Can use Clipboard Key Strokes to get the correct info but is an extra step and slower to paste information.

Change Password screen should offer clarity of minimum requirements and illegal characters
We resell access to ConnectWise Control Access to some of our customers. When we setup accounts we force the user to change their password on first login. Many times we have received questions or experienced some frustration over the process of changing password for the following reasons:
- Lack of clarity of minimum password requirements, not identified or written anywhere (or at least not obviously and clearly)
- Even with the rule of "minimum 8 characters, 1 upper, 1 lower, 1 number, 1 symbol" it is possible to get an error message stating 'invalid password'. Sometimes the password does not change, and sometimes despite the error message the password changes (but only find out after we log out and log back in). This is extremely confusing for both our client users and our NOC technicians. I have personally experienced both scenarios where a complex password I try (a) does not take effect + I receive an error message stating 'invalid password' (which password is invalid? the old password or the new one?) and (b) I receive the error message stating 'invalid password' + my account password changed to the 'invalid password' password (the new one) and the only way to test this is to log out and log back in trying the new password for which I received an error message
Additionally, we have had users encounter 'invalid password' with 2FA setup. They enter their credentials and hit login, then enter their Google Authenticator code and hit submit only to receive an 'invalid password' error.
I apologize in advance as some of what I write and present here is lacking in concrete reproducible steps.

Hey Joshua,
You can edit the web resource ChangePasswordPanel.Description to include password requirements.
Even with the rule of "minimum 8 characters, 1 upper, 1 lower, 1 number, 1 symbol" it is possible to get an error message stating 'invalid password'.
If a user is meeting the password requirements the error shouldn't appear. If that isn't the case, please reach out to our support team so they can investigate.
Sometimes the password does not change, and sometimes despite the error message the password changes (but only find out after we log out and log back in).
Again, if an error is received but the pw is accepted I'd reach out to support so this can be investigated and logged.
Customer support service by UserEcho
