Your comments
I found that the best option is to set LoginPanel.ForgotPasswordLinkVisible to false because that will disable the link entirely rather than just removing the text.
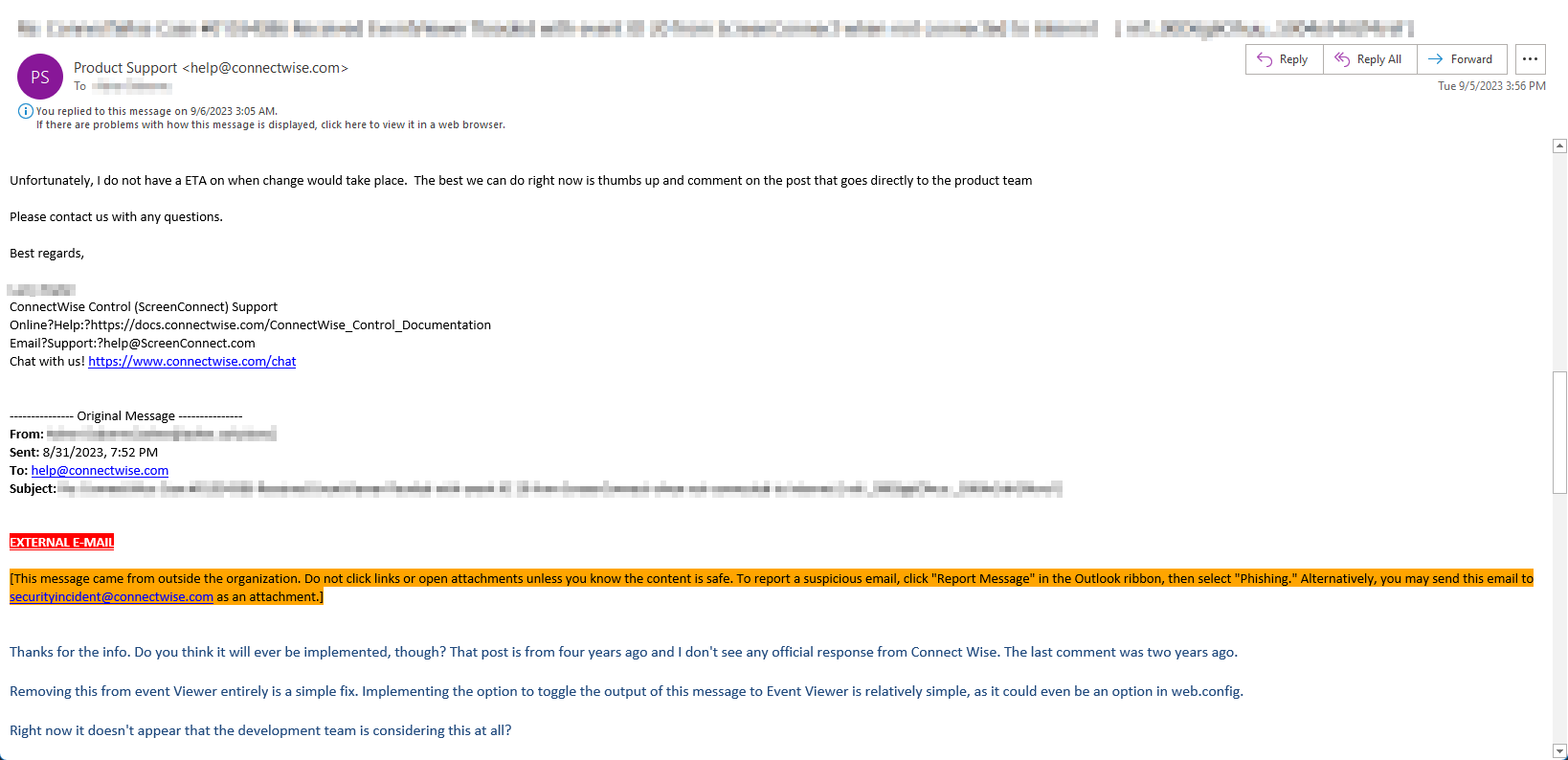
I actually contacted ConnectWise support on this very issue which is how I found this thread. Here's what they said. I asked if it would ever be implemented or if they had an ETA.
May have to right-click Open Image in New Tab to view...
Customer support service by UserEcho


Banning or some type of limit on "number of tries" would be great. Even if it was simple, just blocked the IP for an hour after X number of attacks, that would help. This type of security doesn't seem like it would be too hard to implement into the code.
As a workaround, there are two ways I've found to mitigate unwanted access attempts:
1.) Restrict the login attempts to a list of allowed IP ranges. For IPs that are not static, I've looked up the network range that the IP is in, and allowed that. So although I may have allowed everyone in a certain city or connection, it's better than allowing the entire world. You can find the network range of an IP address on sites like ipinfo.io or arin.net. The allowed list can be changed under Advanced > Web Configuration > Settings > Restrict to IP Addresses.
2.) On another server, I implemented pfSense with pfBlockerNG and blocked IPs outside of the country. Doing that reduced the number of brute force attempts by 90%. Note that doing this can be effective but also adds some layer of complexity to the environment.
Although these fixes don't solve the issue of blocking brute force attacks, it does significantly reduce the attack surface.