Support ALL Duo 2FA authentication methods
The addition of Duo push 2FA is great but a bit puzzling. Why only support push when Duo supports so many authentication options and they make it easy to implement them all.
- Some people don't have a smartphone where they can install the Duo app so push won't work for them but they can still receive a text message of phone call just fine. Duo supports both of these options for 2FA but
Screenconnect'sControl's integration was is implemented in a way that does not allow them. - Some people might have multiple devices with the Duo app installed and need to choose which one they want the push sent to. Duo allows users to choose which one they want to receive a push from, or which one they want to receive a text or call on. Again Control's integration does not allow this.
- Ever forgotten your mobile phone at home? I have and that's why I've configured my Duo account with a hardware token too. Unfortunately Control's integration does not support this Duo 2FA method either.
- Perhaps you are prone to forgetting your mobile device but don't want to have a hardware token. In this case Duo can be configured with bypass code (basically a OTP that you know beforehand). Well, you know the story.
I'd really like to see Control support the all the Duo authentication methods and for the looks of their documentation this should be relatively easy.
https://duo.com/docs/duowebAs an added bonus this also provides a natural way to handle the 2FA logon rather then show the user a prompt for a code that they can't type (what your Duo 2FA currently does).
Answer

2 years in and still nothing? Please hurry up as MFA is mandatory for MSP now.

We need to see duo properly implemented as soon as possible. We're required to have 2FA for PCI-DSS compliance, and not all of our users have Smartphones.

Also we would like duo integrated with the hosted version of Connectwise Control.

Would be great to see DUO fully implemented on Screenconnect ConnectWise on-premise, we currently have a few users that don't have a smartphone & can't use DUO to authenticate to Screenconnect Connectwise.

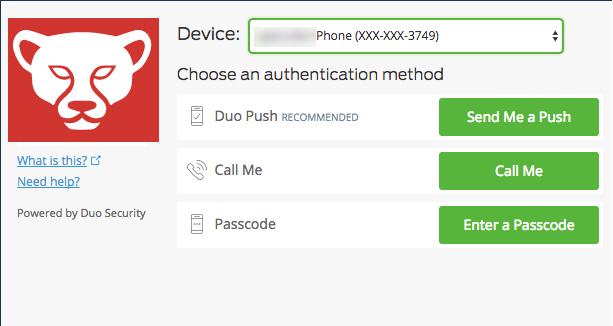
For anybody who hasn't upgraded to the latest release of Control, they do have DUO integration. I have it working. However if you use the Duo Access Gateway, and you click the link you setup on that page for Control, The expected behavior should prompt you with the screenshot above, (Send Me A Push), but it does not. It requires you click the "login with external provider", then you are prompted with "Send me a Push." We think there is a logout url missing in the metadata used when creating the configuration on the DAG. Not 100% sure on that, just something we are speculating on that appears to be missing. Hopefully they will resolve soon. I am on cloud version 6.5.16479. If you are looking to upgrade be cautious, we have Labtech 11 patch 19, and 6.5 is not officially supported on-prem, (but they can get it to work), but the hosted cloud version it definitely doesn't work.
Hoping they resolve the issues soon.

This feature of being able to use the ONE-TIME passcodes is important to us to be able to use our DUO hard tokens. I see this thread was built about 2 years ago. We really need movement in this area. It would really boost security for all our MSPs.

Hi Bill, saw your comment, ScreenConnect supports the full DUO 2 Factor. From the Push, to a one time password, to an sms on your phone, to the bypass code you are asking about. We have it working internally for both the Cloud version of ScreenConnect and our Automate version of it. We are using Duo on our Smart Phones, but the test with the bypass code doesn't rely on that. If an engineer forgets their phone, we setup a bypass code for the day. And they can work.

@mpaul
So you are saying that you can set a bypass code in Duo and use it in the Connectwise Control login process and it works? It does NOT work for me. Are you sure this works for self-hosted installs? Can someone confirm?

The issue we ran into today was regarding the one-time passcode. The Control integration to the best of my knowledge right now uses the PUSH method when you use the [duo: username] field in Active Directory. We tried to connect an AD user who only had access to a DUO HardToken. The hard-token only generates a 6-digit code, which you would assume would be able to be used in the One-Time Password field when authenticating. We went ahead and decided to use the SMS Email notification method, until we hear back regarding the ability to use hardtokens.

We used a workaround. We use DAG to sign on to Azure AD, and we setup SAML SSO with Control to Azure AD. Lot of steps but it works.

Any progress on this feature request? Even as simple as fixing the 2fa screen so it's not confusing to explain that you don't actually enter a OTP code but approve the duo push and click login. Most implementation of duo push have a screen that states waiting for response from push approval then when you approve from device it auto proceeds.

What is the latest with this feature? Current dialog is really sketchy looking.

Connectwise as a whole REALLY needs to step up their security game within their products. They do a whole bunch of lip service to us buying products to SELL security products/services, but their own software is lacking in several areas.

at this point, MFA is mandatory for MSP and still, Control is unable to improve DUO integration. Today we found out the Control Integration is easy to bypass with a fake code(for security reasons We not sharing this method) I already reported this to CW support and what they told me "This function you are talking about is not in there. the only way to get that functionality is the thread" I request to escalate the ticket to report the vulnerability.
Control Support listening up We are the Good Guys and we Found a vulnerability and you Just Ignore us!

Hi Jay,
Can you please email the ticket number from that support discussion to cbarnes@connectwise.com? Thanks!

I just sent you my ticket number (#12324154) where I was told the exact same thing ("the best we can do there is add a comment or upvote the request")

We have to contact the Chief Customer Officer to get this matter resolved
I get a call from the Support and Development team and we were able to identify the vulnerability and fixed the problem but still no support for a hardware token.
All our tech are unable to access Control at the moment(all our systems and app's are set to work with DUO hardware Tokens)

Jay, It was great working with you yesterday. We will be looking at expanding support for Duo to include hardware tokens, but we do not have a timeframe on when we may make that available.
Also, I want to make it clear that this issue was not a Control vulnerability, but instead, the Duo App on the affected users phone was out of date. Once the Duo App was updated, the issue was resolved.
Thanks!
Sean White

Come ON!!!!! My customers are: Capable:They can save passwords on their phones; Mobile: They can access Control from their phones; NOT Paranoid: If they misplace (or think they might have misplaced) their phones, they DO not first call and have the phone wiped, they go looking for it, and that can take precious time! A compromised phone can easily be a ZERO FACTOR AUTHENTICATION METHOD. Hardware tokens are one of the oldest 2fa methods around. This seems to have become a lip service item. Because of it, we have to go to other products to meet our customer's needs. GET IT FIXED, PLEASE!!!!!!!!!

I would simply like the ability to use the OTP option through Duo. The integration is confusing the way it is. A user signs in and gets sent a push notification but is also presented with a OTP box that needs to be left empty.

Ooh, so that's what I'm supposed to do with the OTP box that is there for no reason after configuring duo
Thanks for helping me when support couldn't

How hard could this be? I am ScreenConnect customer and was looking at Automate. I think I will move on, based on the lack of movement on this issue.

Crickets. They have it for Automate.
Apparently somebody much smarter than the rest of us has determined that we don't really need this for Control.
It's not like the program is a HIGH-RISK point of intrusion or anything.
Security?? Nah, your security is good enough...

We cannot use Duo without more options than just push. We cannot require all users have smartphones. I can't believe this has sat for 5 years - Control is a web app for goodness sake! We need to implement 2FA, and so need to look for replacements for Control if this is not implemented soon.

I see no one has posted here in a long time. Did we ever get this fixed? I'm still getting the OTP popup in screen connect. I can ok the log in then hit login on screen connect but it would be nice if the duo prompt came up so you knew what was going on

So just mentioning this from previously. With a Duo token on an IOS smartphone, (not the hardware token), you can support the push notification. No need for an OTP. My screen looks like this. I hit connect with Duo 2FA at the bottom.
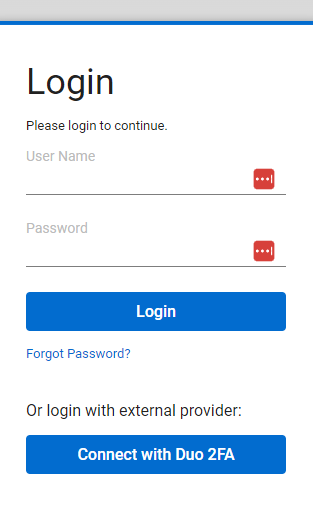
If I have used the Duo SSO page to access, then it does SSO all the way in and I'm not prompted for approval, as I already did all of that with the Duo SSO page.
If I navigate directly to the screenconnect web page, and do Login, I then see the screen shot 1 below. Clicking on the "Connect with Duo 2FA" takes me to my Duo SSO web page. Most of my users use the Duo SSO page to start though.
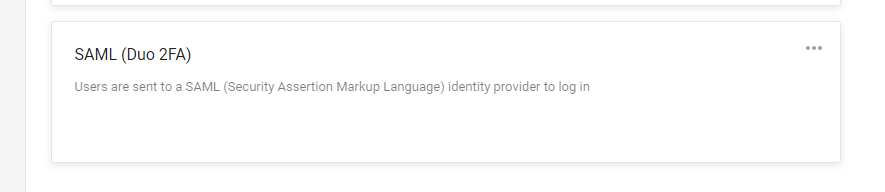
In the Admin page in Duo you configure the SAML integration. Second screenshot.
I don't have any users with hardware tokens, and I know some folks were asking about that one.
I keep mentioning Duo SSO, but this is the replacement to the Duo Access Gateway which was deprecated this past year (by Duo.) It is a service hosted in your Duo portal. You can add any SAML integrated apps, or bookmarks for your organization. See third screenshot just an example.

What about those that keep everything in-house and do not use the Duo SaaS SSO?
If a user does not receive the Duo push notification on his phone, he cannot login to ScreenConnect using the Passcodes from the Duo app. Why display the "One-time Password" form if you cannot use a Duo Passcode?
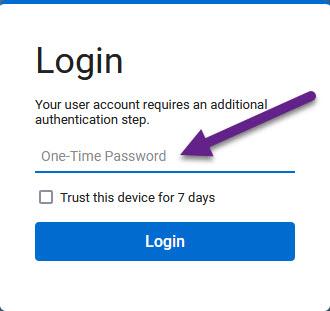


ya kinda weird. I got it to work. It still shows the OTP but it does push an approval to the phone. You just don't enter anything in there and hit login
Customer support service by UserEcho




Jay, It was great working with you yesterday. We will be looking at expanding support for Duo to include hardware tokens, but we do not have a timeframe on when we may make that available.
Also, I want to make it clear that this issue was not a Control vulnerability, but instead, the Duo App on the affected users phone was out of date. Once the Duo App was updated, the issue was resolved.
Thanks!
Sean White